Introduction
In 2024, the digital landscape continues to evolve at an unprecedented pace, bringing forth new innovations and opportunities. However, with these advancements come new and emerging threats, particularly concerning data security. Data leaks have become a significant concern, threatening personal privacy, corporate integrity, and national security. This article explores the rise of data leaks in 2024, examining their causes, impacts, and strategies for prevention.
Understanding Data Leaks
A data leak occurs when sensitive or confidential information is inadvertently exposed to unauthorized individuals. This can happen due to various reasons, including cyberattacks, human errors, or system vulnerabilities. Unlike data breaches, which often involve malicious intent, data leaks can result from a range of issues, from misconfigured databases to simple mistakes.
The Surge in Data Leaks in 2024
1. Increased Cyberattacks
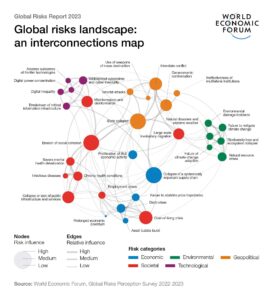
As technology advances, so do the tactics employed by cybercriminals. In 2024, the frequency and sophistication of cyberattacks have surged, leading to a rise in data leaks. Ransomware attacks, phishing schemes, and advanced persistent threats (APTs) have become more prevalent, exploiting vulnerabilities in systems and networks to access and exfiltrate sensitive data.
2. Complex Cloud Environments
The adoption of cloud computing has revolutionized how organizations store and manage data. However, the complexity of cloud environments introduces new risks. Misconfigurations, inadequate security controls, and third-party vulnerabilities can lead to accidental data exposure. The rise in cloud-based data leaks highlights the need for robust cloud security practices.
3. Remote Work Challenges
The shift to remote work, accelerated by the COVID-19 pandemic, has brought about significant changes in how data is accessed and managed. While remote work offers flexibility, it also increases the risk of data leaks. Insecure home networks, personal devices, and insufficient security measures can contribute to accidental or intentional data exposure.
4. IoT and Connected Devices
The Internet of Things (IoT) has interconnected devices, creating new opportunities for data collection and analysis. However, the proliferation of IoT devices also introduces vulnerabilities. Many IoT devices lack adequate security features, making them potential targets for attackers seeking to exploit weaknesses and access sensitive information.
The Impact of Data Leaks
1. Personal Privacy
Data leaks can have severe consequences for individuals, leading to identity theft, financial loss, and personal distress. Exposed personal information can be used for fraudulent activities, phishing attacks, and other forms of exploitation. The impact on personal privacy underscores the need for effective data protection measures.
2. Corporate Reputation
For businesses, data leaks can result in significant reputational damage. Customers and clients expect organizations to safeguard their information, and a data leak can erode trust and lead to a loss of business. The financial repercussions of a data leak can also be substantial, including legal fees, regulatory fines, and remediation costs.
3. National Security
Data leaks can pose risks to national security, particularly when sensitive government or defense information is exposed. Such leaks can compromise intelligence operations, diplomatic relations, and public safety. Ensuring the security of critical data is essential for maintaining national security and preventing potential threats.
Strategies for Preventing Data Leaks
1. Implement Robust Security Measures
Organizations must invest in comprehensive security measures to protect against data leaks. This includes deploying advanced threat detection systems, encryption technologies, and access controls. Regular security audits and vulnerability assessments can help identify and address potential weaknesses.
2. Educate and Train Employees
Human error is a significant factor in data leaks. Providing regular training and awareness programs for employees can help reduce the risk of accidental data exposure. Employees should be educated on best practices for data handling, phishing recognition, and secure password management.
3. Secure Cloud Environments
Organizations using cloud services must ensure that their cloud environments are properly secured. This involves configuring security settings, implementing strong authentication mechanisms, and regularly monitoring cloud activity. Partnering with reputable cloud service providers that prioritize security can also mitigate risks.
4. Adopt a Zero Trust Model
The Zero Trust security model operates on the principle of “never trust, always verify.” This approach involves continuously validating user identities and device security, regardless of their location. By adopting a Zero Trust model, organizations can reduce the risk of unauthorized access and data leaks.
5. Monitor and Respond to Threats
Real-time monitoring and threat detection are crucial for identifying and responding to potential data leaks. Implementing Security Information and Event Management (SIEM) systems and establishing incident response protocols can help organizations quickly address and mitigate the impact of data leaks.
Conclusion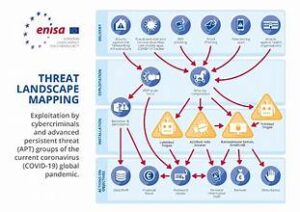
As technology continues to advance, the threat of data leaks remains a pressing concern. The rise in cyberattacks, the complexity of cloud environments, remote work challenges, and IoT vulnerabilities contribute to the increasing prevalence of data leaks in 2024. To protect personal privacy, corporate integrity, and national security, it is essential to implement robust security measures, educate employees, secure cloud environments, adopt a Zero Trust model, and monitor for threats. By taking proactive steps, organizations and individuals can better safeguard their data and mitigate the risks associated with data leaks.